It is often assumed that cyberattacks on IoT devices require specialized skills and advanced tools. However, real-world incidents show that many vulnerabilities can be exploited with surprisingly simple techniques.
In this article, we will explore three real-world IoT attacks and detail the methods and tools used by attackers to compromise the following devices:
1. Wi-Fi Fireworks system Shoot Firefly
2. VStarcam CB73 Security Camera
3. Wyze cam v2 camera
These attack scenarios illustrate how an attacker can achieve full administrative access to IoT devices using only basic tools, such as a serial cable, standard Linux utilities, and free reverse engineering software.
We will also explore the critical security lessons learnt from each of these attacks.

An attacker gains physical access to the fireworks system’s casing and identifies a UART connector on the circuit board, labeled TXD, RXD, and GND—standard pin names for serial communication.
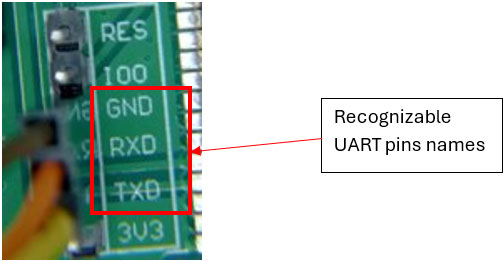
By connecting a serial cable to a computer, the attacker obtains shell access to the system. During boot, the system logs reveal the WiFi SSID and password in plain text.
If users have not changed the default password, an attacker could remotely ignite fireworks, posing a serious security risk.
To control the fireworks device, a mobile phone connects to the WiFi access point mentioned in the logs.
By executing a man-in-the-middle (MITM) attack, the attacker intercepts network traffic and discovers that no encryption or authentication is in place—making communications vulnerable to eavesdropping.
To further analyze the system, the attacker reverse-engineers the Android application, which is easily downloadable from third-party app stores.
Since Android apps are developed in Java, if the application lacks protection, decompiling it reveals the original source code.
Using JADX (a Java decompiler), the attacker quickly finds that the application is not obfuscated, making it easy to understand the communication protocol used to send commands to the fireworks system.
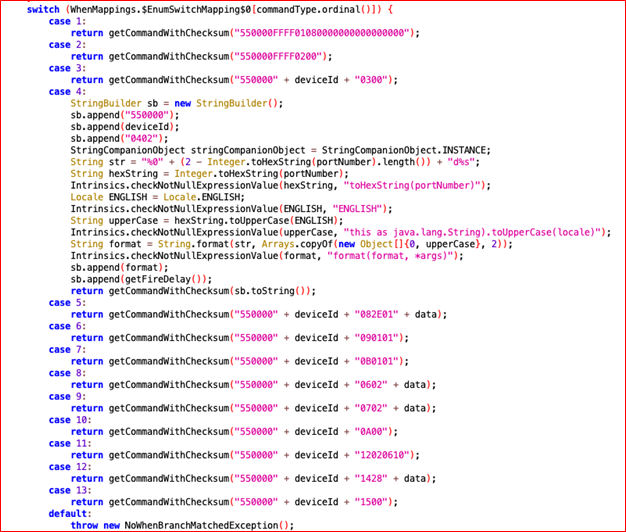
With access to the command structure, the attacker can craft and send malicious commands to any firework device that still uses the default password.
This allows the attacker to ignite fireworks remotely, posing a serious safety risk.
By implementing these security measures, the risk of unauthorized access and remote exploitation of fireworks control systems can be significantly reduced.

VStarcam CB73 is a Chinese security camera for homes, selling below 30 €.
Security researcher Matt Brown presents the attack steps to gain full root access to the device in this video. [2].
The attacker gains access to the camera’s internal hardware by opening its casing and identifying four test pads on the printed circuit board (PCB).
By consulting the processor’s datasheet, the attacker determines that these test pads correspond to UART serial communication pins.

Using a serial cable, the attacker connects these pads to a computer, obtaining access to the device’s terminal. However, the shell prompts for a login and password.
While examining the console logs, the attacker notices that the device uses U-Boot (a common bootloader).
During boot, holding the “Enter” key interrupts the process, opening the boot menu.
By running printenv, the attacker inspects the boot arguments (“bootargs”) and modifies them to boot directly into a shell (/bin/sh) using:setenv bootargs console=ttyS1,115200n8 root=/dev/mtdblock2 init=/bin/sh
Executing the boot command then relaunches the boot sequence, granting access to a restricted shell.
To bypass these restrictions, the attacker examines the device’s initialization scripts (/etc/init.d/rcS).
By running specific Linux commands, the attacker escalates to a fully functional shell with access to the file system.
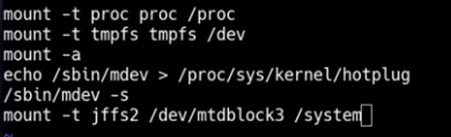
Discovering a Hardcoded Root Password – Hacking the VStarcam CB73 Security Camera, Matt Brown, July 24 2024
Upon inspecting the passwd file (/etc/passwd), the attacker discovers a user account:
vstarcam2017:<hashed password>
Using Hashcat, a password-cracking tool, fails to decrypt the hash.
Searching for occurrences of “passwd” within the filesystem reveals that a binary named “encoder” writes to /etc/passwd.
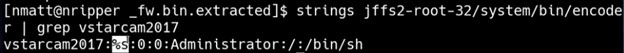
Disassembling this binary using Ghidra (a free reverse engineering tool) reveals that it contains a hardcoded password:
20170912
After rebooting the device, the attacker successfully logs in using:
vstarcam201720170912This grants root shell access, providing full control over the camera.
By implementing these security measures, the risk of unauthorized access and device compromise can be significantly reduced.

Wyze cam cameras are affordable surveillance cameras for homes, selling for around 25€.
In this video, security researcher Stacksmashing presents the attack steps needed to modify the camera’s firmware and inject a backdoor [3].
The attacker begins by downloading the camera’s firmware directly from the manufacturer’s website, as no authentication or registration is required.
Using standard Linux tools such as binwalk, the attacker unpacks the firmware and locates the Linux shadow file, which contains password hashes.
By running the John the Ripper password-cracking tool, the attacker quickly retrieves the plaintext password.
After gaining access to the firmware’s file system, the attacker modifies key system files (e.g., /etc/init.d/rcS) to integrate a backdoor.
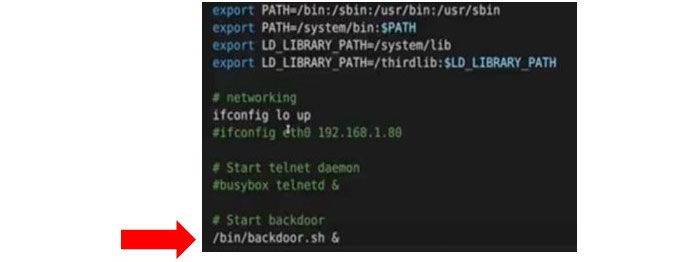
This backdoor enables the camera to call back a command-and-control (C2) server, allowing the attacker to remotely control the device.
The attacker then repackages the modified firmware using standard Linux tools and installs it on the camera via the official upgrade process.
Since the manufacturer does not verify firmware integrity or authenticity, the device accepts the modified firmware without issue.
With the backdoor in place, the attacker can now connect to the camera remotely via the C2 server.
This access allows them to:
For example, the attacker could sell the compromised camera second-hand, gaining persistent access to the buyer’s home or corporate network.
By enforcing strong cryptographic protections and strict authentication measures, manufacturers can prevent unauthorized firmware modifications and secure IoT devices against remote takeovers.
These three attacks illustrate how an attacker can achieve full administrative access to IoT devices using only basic tools, such as a serial cable, standard Linux utilities, and free reverse engineering software.
In the final scenario, the attacker goes a step further by modifying the firmware to implant malicious code, enabling persistent remote control of the device. This situation underscores the urgent need for stronger security measures in embedded systems to prevent unauthorized access and firmware manipulation.
Our audit and consulting team, QLab, made up of expert security engineers and researchers, can perform security audits on devices and software to help you spot vulnerabilities.
QShield, a comprehensive suite of security solutions, can help you protect firmware and applications with obfuscation, anti-tampering, and Runtime Application Self Protection RASP.
Get in touch to learn more.
[1] Hacking a WiFi Fireworks Firing System – The FireFly Plus, Matt Brown https://www.youtube.com/watch?v=gHu3upXJT0U
[2] Discovering a Hardcoded Root Password – Hacking the VStarcam CB73 Security Camera, Matt Brown https://www.youtube.com/watch?v=lbSalKp_ldA
[3] IoT Security: Backdooring a smart camera by creating a malicious firmware upgrade, stacksmashing https://www.youtube.com/watch?v=hV8W4o-Mu2o